One major topic in Learning Tree Course 468 System and Network Security Introduction is that of encryption. It is a core technology in cyber security because it is used to secure confidential data, as well as protect passwords and the integrity of documents.
There are two basic families of encryption used to ensure the confidentiality of data: symmetric and asymmetric. Symmetric encryption uses one key (a number) to encrypt and decrypt (undo the encryption of) a message. It is generally a large random number. Asymmetric (public key) encryption uses different keys for encryption and decryption That is, one large number is used to encrypt the data and a different large number is used to decrypt the data. The numbers are computed at the same time and are mathematically related.
In a public key system, each user has two keys: a public key shared with others and used to encrypt confidential messages to that user, and a private key used to decrypt those messages and not shared with anyone.
Encrypting For Multiple Recipients
Here, I will be writing about senders and recipients; that's to make things easy. In reality, this also applies to stored files. Stored data is called data at rest, and data being sent from one place to another is called data in motion. An example of the latter is email.
Let's assume I want to send an email message to both Carlos and Hannah. I want the message to be confidential so if someone gets a copy of that message, they cannot read it. Only Carlos and Hannah should be able to read it.
I could use symmetric encryption and encrypt the message twice: once for Carlos and once for Hannah. Sure, I could the same key for each of them, but that does not scale well. If I wanted to easily send the message to one hundred recipients, I'd have to share the same key with each of them. If I no longer wanted one of those hundred to read future messages I might want to send to the group, I'd have to send out a new key to everyone. It is difficult, if not impossible to send that key to those hundred in such a way that nobody else could intercept it. It would be better, then to have a separate key for each recipient.
But having a separate key for each recipient doesn't scale well, either. With a hundred recipients, I'd need to encrypt a hundred times. The two times for Carlos and Hanna is one thing, but a hundred would be hard to manage.
What I need is a fast method, lets me encrypt the message just once, and scales well for small or large numbers of recipients. One method of doing this is used by RSA, PGP, and S/MIME. The basic idea is to encrypt the actual message with a symmetric (random) key and then encrypting that key for each recipient using his or her public key. See the image below.
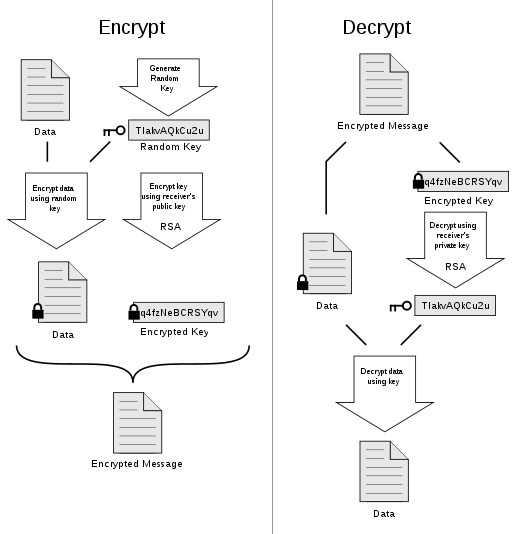
xaedes & jfreax & Acdx, CC BY-SA 3.0 <https://creativecommons.org/licenses/by-sa/3.0>, via Wikimedia Commons
This illustration shows only a single "Encrypted Key" but in our case, we'd have one key for each recipient. Because we use both symmetric and asymmetric encryption together, we call this a hybrid cryptosystem.
This scales well because the encrypted key is a small number compared to the message. If we were to use this for email, we'd send the encrypted data and encrypted key(s) in the email. (We'd also send some other stuff such as the encryption type used.)


